Users authentication with OpenID and Keycloak
This instruction is valid only for the server version of Allure TestOps, starting with version 5.6.4.
OpenID support in the cloud version of Allure TestOps is planned by the end of Q1 2025.
Allure TestOps implements standard Spring Boot OpenId client.
Prerequisites
To successfully configure and use OpenID with Keycloak you need to meet the following requirements.
- You need to have administrative access to Keycloak or a Keycloak admin near you during the configuration process.
- You need the access to Allure TestOps configuration files.
- You need to be able to apply the changes in the configuration, which could require some downtime.
- Both Keycloak and Allure TestOps need to use the same protocol for the communication, i.e. if one of the systems works behind HTTPS, then both systems need to work behind HTTPS, i.e. there must be something like reverse proxy that will allow using of HTTP between Allure TestOps and Keycloak servers. Please consult your network administrator or DevOps to ensure proper configuration on the network side.
Integration of Allure TestOps and Keycloak
Further examples will use fake addresses that in your case will differ.
Let's assume the following.
- Allure TestOps is deployed and accessible on http://allure.local
- Keycloak is deployed and accessible on http://keycloak.local
Sequence
What needs to be done assuming we need to sync Keycloak groups with Allure TestOps global roles.
- Create a new realm on Keycloak side (optional).
- Create OpenID client on Keycloak side in the realm you are going to use (mandatory).
- Define realm roles and groups.
- Define client scopes.
- Add users and assign roles and groups.
- Perform the configuration on Allure TestOps side.
Setting up Keycloak side
Optionally, create a new realm on Keycloak
Create a new realm, if you want Allure TestOps uses to reside in a separate Realm.
Create new OpenID client for Allure TestOps
Allure TestOps will be a OpenID client for Keycloak.
- Switch to the realm that is intended to work with Allure TestOps.
- Go to Clients section in Keycloak UI and click Create client
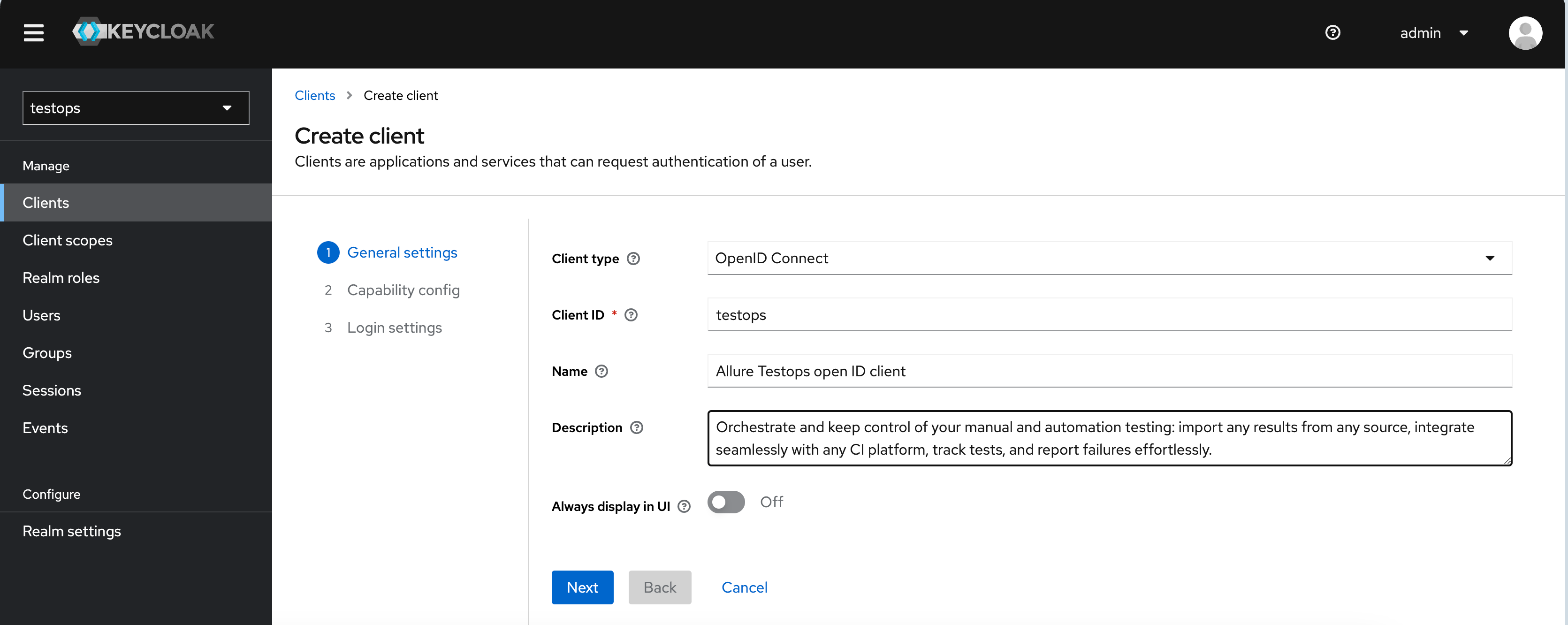
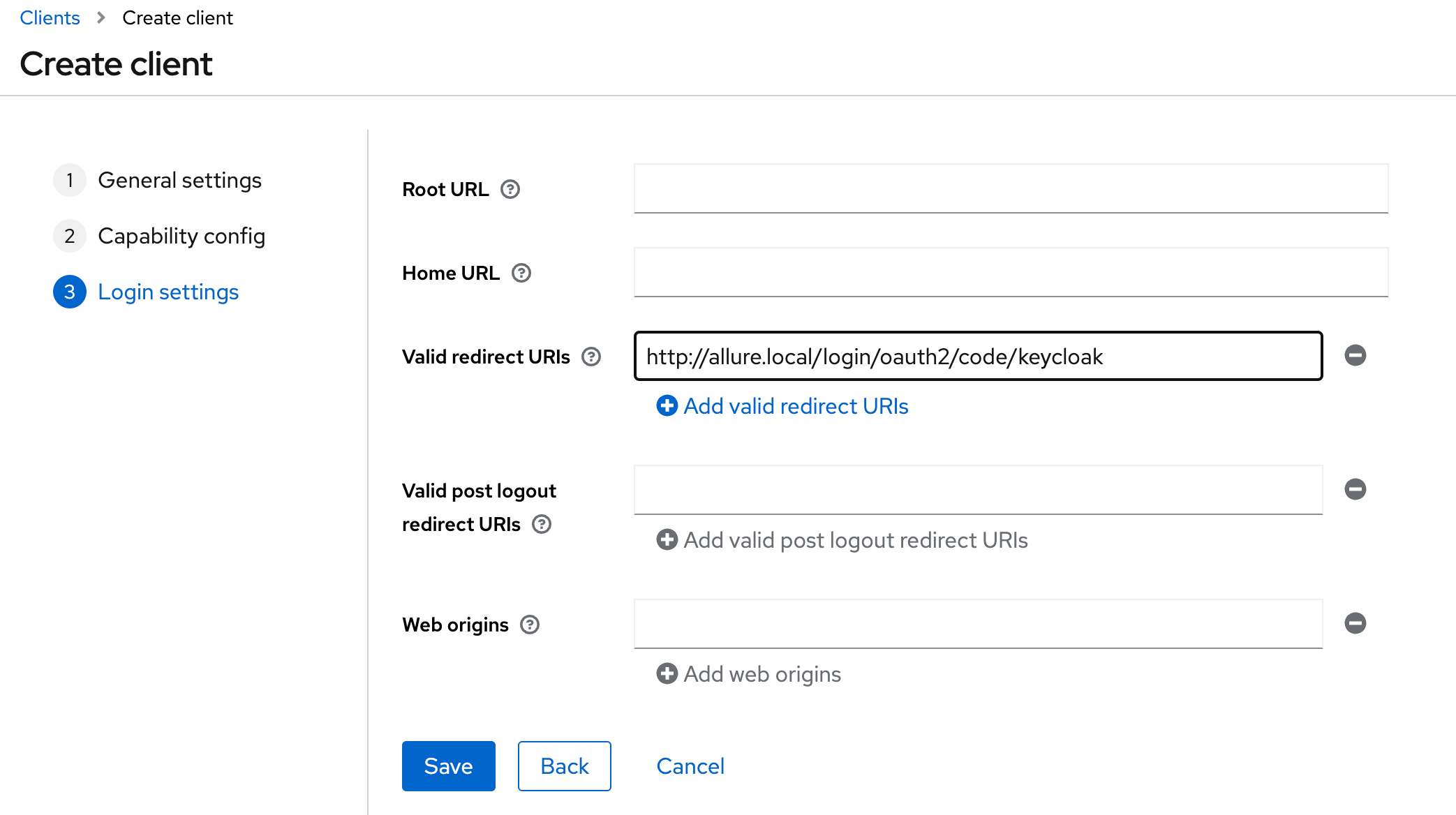
- When creating a new client, set Valid Redirect URIs: http://allure.local/login/oauth2/code/keycloak
- Finalise the configuration by saving the newly created client's data.
Define realm roles and groups
This step is required if you want to sync Keycloak's groups with Allure TestOps global roles, i.e. the members of a certain group in Keycloak will get Allure TestOps global roles
ROLE_ADMINorROLE_USER.Allure TestOps syncs global roles with the groups on Keycloak side.
On Keycloak side, create two roles, one for the group of users who will be admins on Allure TestOps side and another for the group. In our example we'll use role and ato_admins for the Allure TestOps users who supposed to be administrators (ROLE_ADMIN) and ato_users for those who are going to get a simple user role (ROLE_USER).
- Go to Realm roles in the Realm where Allure TestOps is registered as OpenID client.
- Create 2 roles
ato_adminsato_users
- Go to Groups
- Create 2 groups
ato_adminsato_users
- Go to
ato_adminssetting Role mappings- add
ato_adminsrole to the list of roles
- add
- Go to
ato_userssetting Role mappings- add
ato_usersrole to the list of roles
- add
Now, we have 2 groups which have assigned roles.
Define client scopes
For the information about assigned groups for a certain user to be accessible for Allure TestOps, we need to add a new scope to Allure TestOps as OpenId client on Keycloak side.
- Go to the Client scopes
- Click Create client scope
- Name the scope (we'll name the scope
groupsfor the sake of the example).- assign Default type to the scope being created.
- Check Include in the token scope as we need this information to be available for Allure TestOps in the access token (see below).
- Go to the settings of the created scope
- Switch to the Mappers tab
- Click Add mapper and in drop-down select from predefined mappers.
- Check a mapper called groups and make this scope to default one.
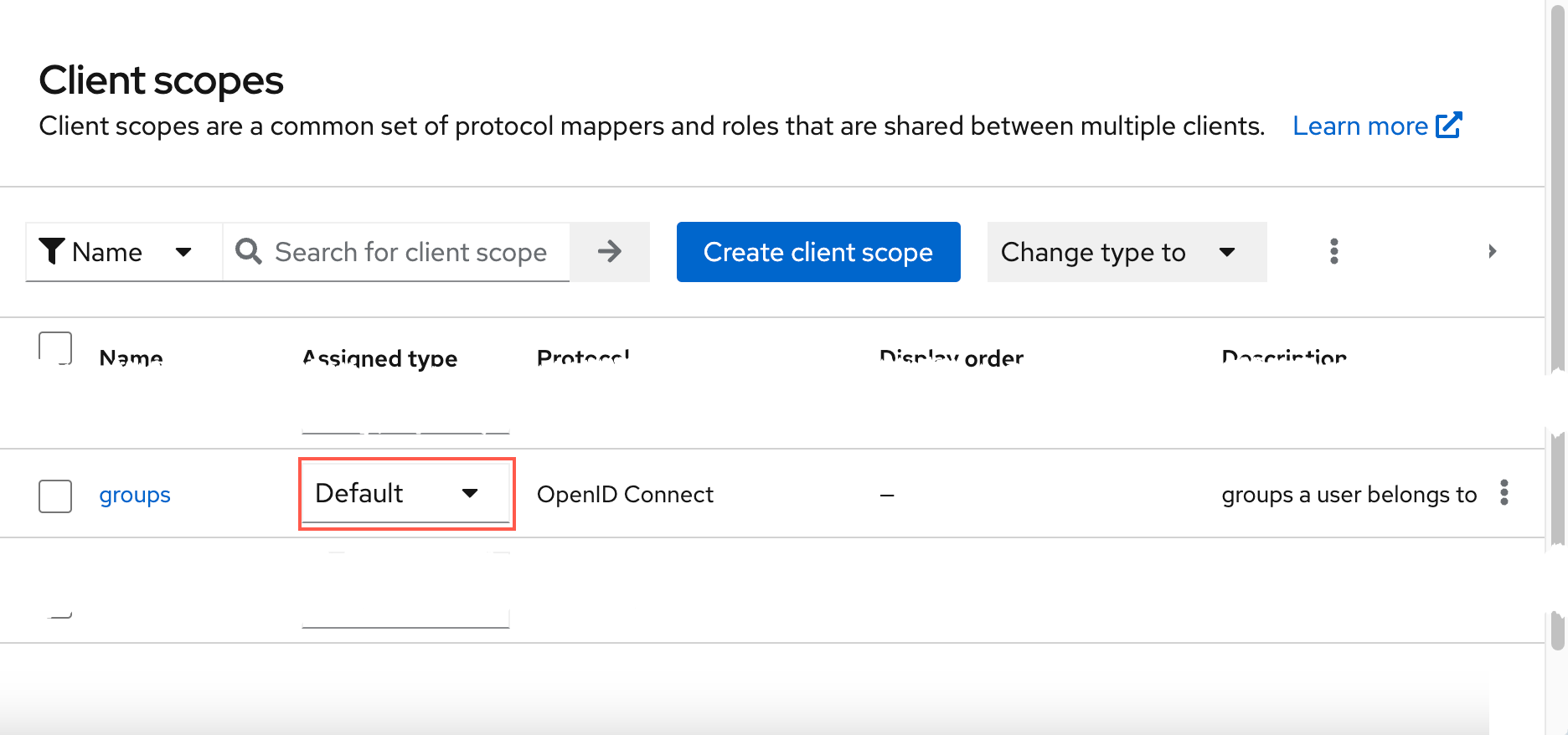
Check the content of access token
You can try to get the access token from Keycloak. This exercise could be useful during the troubleshooting if anything goes south with the roles synching. So, for now, you can easily skip this step.
Allure TestOps will receive the access token form Keycloak upon the successful authentication attempt. The access token will contain the information about the user that logs in to Allure TestOps using Keycloak as an Identity provider (or IAM).
Execute the API call using curl or any other tool you are accustomed to.
USERNAME=name of any user registered in Keycloak for Allure TestOps OpenId
U_PASSWORD=password for the user above
CLIENT_ID=testops
RESPONSE=$(curl -X POST 'http://keycloak.local/realms/testops/protocol/openid-connect/token' \
--data-urlencode "client_id=${CLIENT_ID}" \
--data-urlencode 'grant_type=password' \
--data-urlencode 'scope=openid' \
--data-urlencode "username=${USERNAME}" \
--data-urlencode "password=${U_PASSWORD}")
ACCESS_TOKEN=$(echo $RESPONSE | jq .access_token)
echo "$ACCESS_TOKEN"
then you need to decode the received access token, e.g. using JWT debug tool.
Then perform formatting of the JSON content (we deleted content which has no interest for sake of clarity).
{
"exp": 1703517143,
"iat": 1703516843,
"jti": "62b7bd96-a982-4063-9c97-f12dbe1553f8",
"iss": "http://keycloak.local/realms/testops",
"typ": "Bearer",
"azp": "testops",
"acr": "1",
"scope": "openid profile email groups",
"sid": "043242d3-3c67-4ad7-8795-46c0df9f745e",
"email_verified": true,
"name": "Bugs Bunny",
"groups": [
"default-roles-testops",
"ato_admins",
"offline_access",
"uma_authorization"
],
"preferred_username": "bugsbunny",
"given_name": "Bugs",
"family_name": "Bunny",
"email": "[email protected]"
}
So, the scope groups contains the information on the group ato_admins, it'll be used for the sync roles feature.
Add users and assign roles and groups
Now, you need to add Keycloak users and distribute them between the appropriate groups to synch their groups in KeyClock with Allure TestOps global roles.You can skip this step, if you are going to manage the global roles in Allure TestOps.
Perform the configuration on Allure TestOps side
Get OpenID provider endpoints
For proper integration between an OpenID provider and Allure TestOps as an OpenID client, only three endpoints need to be configured on the Allure TestOps side:
- tokenUri,
- jwksSetUri,
- authorizationUri.
To obtain these URI parameters, go to the Realm settings section in Keycloak. In the General tab, locate the Endpoints section and click the OpenID Endpoint Configuration link. This link will direct you to the page http://keycloak.local/realms/testops/.well-known/openid-configuration, which is a JSON file containing all the endpoints for the current Realm.
{
"issuer": "http://keycloak.local/realms/testops-realm",
"authorization_endpoint": "http://keycloak.local/realms/testops-realm/protocol/openid-connect/auth",
"token_endpoint": "http://keycloak.local/realms/testops-realm/protocol/openid-connect/token",
"introspection_endpoint": "http://keycloak.local/realms/testops-realm/protocol/openid-connect/token/introspect",
"userinfo_endpoint": "http://keycloak.local/realms/testops-realm/protocol/openid-connect/userinfo",
"end_session_endpoint": "http://keycloak.local/realms/testops-realm/protocol/openid-connect/logout",
"frontchannel_logout_session_supported": true,
"frontchannel_logout_supported": true,
"jwks_uri": "http://keycloak.local/realms/testops-realm/protocol/openid-connect/certs",
"check_session_iframe": "http://keycloak.local/realms/testops-realm/protocol/openid-connect/login-status-iframe.html",
"grant_types_supported": [
"authorization_code",
"implicit",
"refresh_token",
"password",
"client_credentials",
"urn:openid:params:grant-type:ciba",
"urn:ietf:params:oauth:grant-type:device_code"
],
"acr_values_supported": [
<...>
}
From the opened page, you will need the following endpoints:
- token_endpoint,
- jwks_uri,
- authorization_endpoint.
Configuring Allure TestOps to use Keycloak with OpenID
The configuration process varies depending on the selected deployment type, and the parameter names may differ slightly from the end user’s perspective.
Below, we describe the parameters for officially supported deployments and the configuration parameters described in the deployment section.
Client configuration
For Kubernetes deployment, you need to configure the integration with Keycloak via the variables in the auth.openid section of values.yaml file.
In the previous steps, we gathered the information for the OpenID IdP endpoints. These endpoints correspond to the Allure TestOps parameters as follows:
- token_endpoint →
auth.openid.tokenUri, - jwks_uri →
auth.openid.jwksSetUri, - authorization_endpoint →
auth.openid.authorizationUri.
auth:
primary: openid
defaultRole: ROLE_GUEST
<snip>
openid:
enabled: true
clientName: prod-testops
clientId: prod-testops
providerName: keycloak
clientSecret: "secret-text"
redirectUri: https://testops.demo/login/oauth2/code/keycloak
scope: openid, email, profile
authorizationGrantType: authorization_code
authorizationUri: http://keycloak/realms/testops-realm/protocol/openid-connect/auth
jwksSetUri: http://keycloak/realms/testops-realm/protocol/openid-connect/certs
tokenUri: http://keycloak/realms/testops-realm/protocol/openid-connect/token
usernameAttribute: preferred_username
defaultRole: ROLE_GUEST
syncRoles: false
groupRoleAttribute: groupRoleAttribute
roleUserGroups: ato_users
roleAdminGroups: ato_admins
# the following parameters need to be kept empty
userinfoUri:
firstNameAttribute:
lastNameAttribute:
If OpenID via Keycloak is supposed to be the default authentication method for users in Allure TestOps, the parameter auth.primary needs to be set to openid:
auth:
primary: openid
Once configured, the access by built-in admin needs to be done via the URI: http://allure.local/login/system.
We highly recommend setting the default global role of the users logging in to Allure TestOps first time to ROLE_GUEST. Therefore, the defaultRole parameter should be set as follows:
allure:
<...>
auth:
<...>
defaultRole: ROLE_GUEST
This approach will provide you better control over the license consumption, as ROLE_GUEST does not provide any write permissions in the system and does not consume a seat included in your license.
The synchronization of role attributes will be explained in the next section.
To use OpenID with Docker Compose deployment, you need to use the configuration located in the testops-openid folder.
Map the OpenID endpoints as follows:
- token_endpoint →
TESTOPS_OPENID_TOKENURI, - jwks_uri →
TESTOPS_OPENID_JWKSETURI, - authorization_endpoint →
TESTOPS_OPENID_AUTHORIZATIONURI.
The final configuration will look like follows:
TESTOPS_OPENID_CLIENTNAME=testops
TESTOPS_OPENID_CLIENTID=<YOUR_CLIENT_ID>
TESTOPS_OPENID_CLIENTSECRET=<YOUR_CLIENT_SECRET_HERE>
TESTOPS_OPENID_REDIRECTURI=http://<your-testops-domain>/login/oauth2/code/openid
TESTOPS_OPENID_SCOPE=openid,email,profile
TESTOPS_OPENID_USERNAMEATTRIBUTE=preferred_username
TESTOPS_OPENID_AUTHORIZATIONGRANTTYPE=authorization_code
TESTOPS_OPENID_TOKENURI=http://<open_id_provider_url>/somepath/token
TESTOPS_OPENID_JWKSETURI=http://<open_id_provider_url>/somepath/keys
TESTOPS_OPENID_AUTHORIZATIONURI=http://<open_id_provider_url>/somepath/openid-connect/auth
TESTOPS_OPENID_FIRSTNAMEATTRIBUTE: first_name
TESTOPS_OPENID_LASTAMEATTRIBUTE: last_name
TESTOPS_OPENID_DEFAULTROLE=ROLE_GUEST
TESTOPS_OPENID_SYNCROLES=false
TESTOPS_OPENID_GROUPROLEATTRIBUTE=group
TESTOPS_OPENID_GROUPAUTHORITIES_ROLEUSERGROUPS=roleUserGroups
TESTOPS_OPENID_GROUPAUTHORITIES_ROLEADMINGROUPS=roleAdminGroups
For Linux packages installation to be able to communicate with OpenID provider, modify the configuration file located at /opt/testops/conf/testops.conf. By default, the settings for OpenID support are commented out. To enable OpenID, locate and uncomment the following settings, and set them with the appropriate OpenID endpoints:
- token_endpoint →
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_TOKENURI, - jwks_uri →
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_JWKSETURI, - authorization_endpoint →
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_AUTHORIZATIONURI.
# set
ALLURE_LOGIN_PRIMARY: openid
ALLURE_LOGIN_OPENID_DEFAULTROLE=ROLE_GUEST
# name of Allure TestOps as the OpenID client as it's is defined in Keycloak
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_CLIENTNAME=testops
# ID of Allure TestOps as the OpenID client as it's is defined in Keycloak, used for client authentication
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_CLIENTID=aaabbb-aaa-aaabbb12345-1234
# Secret of Allure TestOps as the OpenID client as it's is defined in Keycloak, used for client authentication
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_CLIENTSECRET=authentication-secret-generated-by-openid-provider
# the part `/login/oauth2/code/openid` is fixed, the part https://allure-testops-instance-url depends on your Keycloak deployment
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_REDIRECTURI=https://allure-testops-instance-url/login/oauth2/code/openid
# leave as it is
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_SCOPE=openid,email,profile
# leave as it is
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_AUTHORIZATIONGRANTTYPE=authorization_code
# check in the openid provider metadata: authorization_endpoint
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_AUTHORIZATIONURI=http://<open_id_provider_url>/somepath/openid-connect/auth
# check in the openid provider metadata: jwks_uri
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_JWKSETURI=http://<open_id_provider_url>/somepath/keys
# check in the openid provider metadata: token_endpoint
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_TOKENURI=http://<open_id_provider_url>/somepath/token
# usually preferred_username
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_USERNAMEATTRIBUTE=preferred_username
# define the name of the claim, containing the name (first name) of the user being authenticated
ALLURE_LOGIN_OPENID_FIRSTNAMEATTRIBUTE=first_name
# define the name of the claim, containing the surname (last name) of the user being authenticated
ALLURE_LOGIN_OPENID_LASTAMEATTRIBUTE=last_name
# these parameters are for the usage with OpenID IdP groups to assign the global roles to users
# depending on the membership in OpenID provider groups
ALLURE_LOGIN_OPENID_SYNCROLES=false
# next parameters need to be uncommented only if ALLURE_LOGIN_OPENID_SYNCROLES=true
# name of the claim defining the groups membership
ALLURE_LOGIN_OPENID_GROUPROLEATTRIBUTE=groups
# name of the openid group with TestOps Users
ALLURE_LOGIN_OPENID_GROUPAUTHORITIES_ROLEUSERGROUPS=ato_users
# name of the openid group with TestOps Admins
ALLURE_LOGIN_OPENID_GROUPAUTHORITIES_ROLEADMINGROUPS=ato_admins
Sync Roles configuration
Motivation
Why do we need synching roles with Keycloak?
Sync of the roles provides you better control over the licence consumption, and prevents end users getting unauthorised access to Allure TestOps projects and you can manage access to Allure TestOps using the features of your Identity Provider.
How it works
On the Identity Provider side, you need to create a group. Then, on the Allure TestOps side, you need to configure the mapping of users to these groups. Based on the membership in these groups, Allure TestOps will assign a global role to the user.
You cannot map end uses to access groups with this synchronization.
Sync roles configuration
- On Keycloak side you need to have Roles and Groups configured.
- Groups must be present in client scopes
For Kubernetes deployment, all settings need to be configured in the auth.openid.syncRoles section of the values.yaml file.
Below are the settings for the OpenID section in values.yaml:
auth:
primary: openid
defaultRole: ROLE_GUEST
openid:
enabled: true
<...>
defaultRole: ROLE_GUEST
syncRoles: true
groupRoleAttribute: groups
roleUserGroups: ato_users
roleAdminGroups: ato_admins
<...>
For Allure TestOps to synchronize global roles with Keycloak groups, the following parameters need to be set:
auth.openid.syncRoles- set to
true
- set to
auth.openid.groupRoleAttribute- name of the claim containing groups of the user being authenticated by Keycloak. We've discussed it here.
auth.openid.roleUserGroups- group name with the Keycloak users that must get Allure TestOps global role
ROLE_USER
- group name with the Keycloak users that must get Allure TestOps global role
auth.openid.roleAdminGroups- group name with the Keycloak users that must get Allure TestOps global role
ROLE_ADMIN
- group name with the Keycloak users that must get Allure TestOps global role
The roles synchronization will only function properly if
auth.openid.defaultRoleis set toROLE_GUEST.
For the Docker Compose deployment, all settings need to be configured for the following parameters:
<...>
TESTOPS_OPENID_DEFAULTROLE=ROLE_GUEST
TESTOPS_OPENID_SYNCROLES=true
TESTOPS_OPENID_GROUPROLEATTRIBUTE=group
TESTOPS_OPENID_GROUPAUTHORITIES_ROLEUSERGROUPS=ato_users
TESTOPS_OPENID_GROUPAUTHORITIES_ROLEADMINGROUPS=ato_admins
<...>
TESTOPS_OPENID_SYNCROLES- set to
true
- set to
TESTOPS_OPENID_GROUPROLEATTRIBUTE- name of the claim containing groups of the user being authenticated by Keycloak. We've discussed it here.
TESTOPS_OPENID_GROUPAUTHORITIES_ROLEUSERGROUPS- group name with the Keycloak users that must get Allure TestOps global role
ROLE_USER
- group name with the Keycloak users that must get Allure TestOps global role
TESTOPS_OPENID_GROUPAUTHORITIES_ROLEADMINGROUPS- group name with the Keycloak users that must get Allure TestOps global role
ROLE_ADMIN
- group name with the Keycloak users that must get Allure TestOps global role
The roles synchronization will only function properly if
TESTOPS_OPENID_DEFAULTROLEis set toROLE_GUEST.
For the DEB or RPM packages deployment, all settings need to be configured for the following parameters:
<...>
ALLURE_LOGIN_OPENID_DEFAULTROLE=ROLE_GUEST
ALLURE_LOGIN_OPENID_SYNCROLES=true
ALLURE_LOGIN_OPENID_GROUPROLEATTRIBUTE=groups
ALLURE_LOGIN_OPENID_GROUPAUTHORITIES_ROLEUSERGROUPS=ato_users
ALLURE_LOGIN_OPENID_GROUPAUTHORITIES_ROLEADMINGROUPS=ato_admins
<...>
ALLURE_LOGIN_OPENID_SYNCROLES- set to
true
- set to
ALLURE_LOGIN_OPENID_GROUPROLEATTRIBUTE- name of the claim containing groups of the user being authenticated by Keycloak. We've discussed it here.
ALLURE_LOGIN_OPENID_GROUPAUTHORITIES_ROLEUSERGROUPS- group name with the Keycloak users that must get Allure TestOps global role
ROLE_USER
- group name with the Keycloak users that must get Allure TestOps global role
ALLURE_LOGIN_OPENID_GROUPAUTHORITIES_ROLEADMINGROUPS- group name with the Keycloak users that must get Allure TestOps global role
ROLE_ADMIN
- group name with the Keycloak users that must get Allure TestOps global role
The roles synchronization will only function properly if
ALLURE_LOGIN_OPENID_DEFAULTROLEis set toROLE_GUEST.