Users authentication with OpenID and Azure AD
This instruction is valid only for the server version of Allure TestOps, starting with version 5.8.1.
Prerequisites
- You need to have administrative access to your Azure AD or an admin available to assist you.
- You need access to the Allure TestOps configuration files.
- You need to be able to apply changes to the Allure TestOps configuration. Changes may require some downtime.
- Allure TestOps needs to run behind HTTPS. This means there must be a reverse proxy or similar system between Allure TestOps and Azure AD instances. Please consult your network administrator or DevOps engineer to ensure proper configuration on the network side.
Integration of Allure TestOps and Azure AD
Please make sure that the following conditions are met prior to proceeding:
- Allure TestOps is deployed and accessible via an HTTPS URL. The examples below use
https://testops.example.com. - Your Azure AD instance settings are available in the Azure portal.
Perform configuration on Azure AD side
Follow all the preparation steps for the integration according to the Microsoft guide:
Create an Azure Active Directory B2C resource.
Create an Azure AD B2C Tenant.
This step will result in the creation of your new Active Directory.
Registry a new application which will be an OpenID client.
Create a secret that registered users will use for the authentication in the Active Directory.
Configure the redirect URI on Azure AD side
Create the redirect URI associated with your Allure TestOps deployment. The URI must consist of three parts:
URL of your Allure TestOps instance. For example, https://testops.example.com;
fixed part /login/oauth2/code/;
suffix with the provider name:
- For Docker Compose and Linux packages deployments, the suffix is openid.
- For Kubernetes deployment, the suffix can be set by the parameter
providerNamein the values.yaml file. Please remember that the provider name mustn't contain either spaces or special characters, that is, it should be one word.
The final string will look like the example https://testops.example.com/login/oauth2/code/openid.
Add the valid redirect URI to the configuration of the created application:
- From the home page of the Azure portal, go to the Azure AD B2C resource.
- In the Manage pane, select App registrations and then go to the All applications tab.
- Choose the application you created using the Microsoft guide.
- In the Manage pane, select Authentication.
- Add the redirect URI you created in the previous step.
- Save your changes.
Get Azure AD OpenID endpoints
After completing the actions described in the Microsoft guide, you'll have the following parameters ready for integrating your Allure TestOps instance with your Azure AD tenant:
- application (client) ID,
- client secret,
- OpenID Connect metadata (the endpoints needed for Allure TestOps configuration):
- authorization endpoint (URI),
- JWKS endpoint (URI),
- token endpoint (URI).
All endpoints used by OpenID flows are accessible from your AzureAD B2C tenant. Follow these steps to copy them:
From the home page of the Azure portal, go to the Azure AD B2C resource.
In the Manage pane, select App registrations and then go to the Endpoints tab.
In the opened panel, find the Microsoft Entra ID OpenID Connect metadata document.
Copy the document's URL and paste it into your browser.
On the resulting page, you will see the metadata related to your AD tenant.
Find and copy the following endpoints from the page:
- authorization_endpoint — generated with the template https://login.microsoftonline.com/<tenant-id>/oauth2/v2.0/authorize;
- jwks_uri — generated with the template https://login.microsoftonline.com/<tenant-id>/discovery/v2.0/keys;
- token_endpoint — generated with the template https://login.microsoftonline.com/<tenant-id>/oauth2/v2.0/token.
Get Azure AD OpenID metadata
To configure your Allure TestOps instance as an OpenID client, you need to get the ID and client secret from the application (OpenID client) created in your Azure AD tenant.
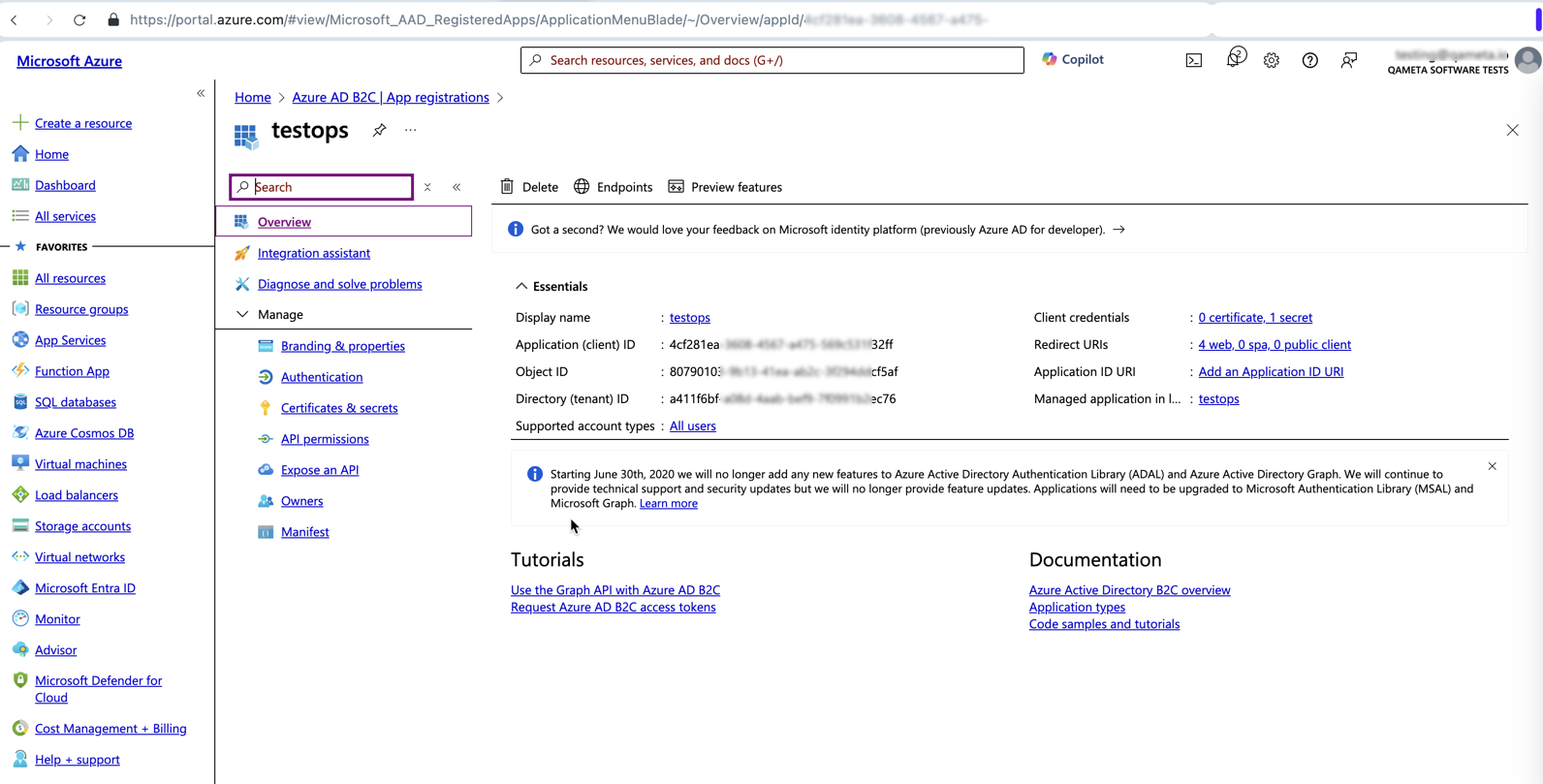
Application ID
- From the home page of the Azure portal, go to the Azure AD B2C resource.
- In the Manage pane, select App registrations and then go to the All applications tab.
- Choose the application you created using the Microsoft guide.
- In the Essentials section, copy the Application (client) ID.
Client secret
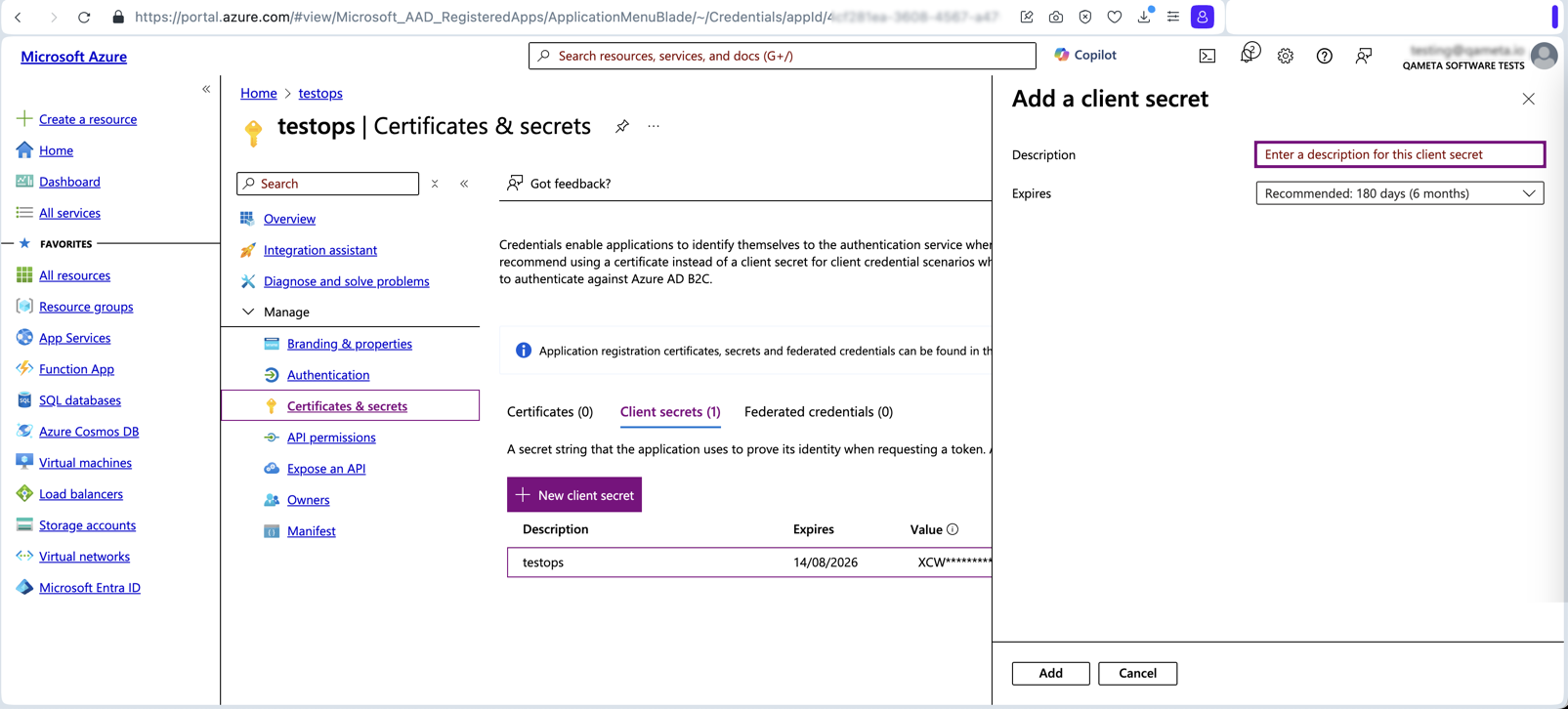
- Start from the previous step where you obtained the Application (client) ID.
- Click the link next to Client Credentials in the Essentials section or select Certificates & Secrets in the Manage pane.
- Click New client secret.
- Set the secret's expiration date.
- Copy the value of the generated secret and save it in a safe place. You will need this value when configuring Allure TestOps.
Configure Allure TestOps
Сonfigure the integration with Azure AD in the auth.openid section of the values.yaml file.
# This is an example that will not work if applied without any changes.
auth:
primary: openid
# ...
openid:
enabled: false
providerName: azure
clientName: testops
clientId: <your-client-id>
clientSecret: <your-client-secret>
redirectUri: https://testops.example.com/login/oauth2/code/azure
scope: openid, email, profile
authorizationGrantType: authorization_code
authorizationUri: https://login.microsoftonline.com/<tenant-id>/oauth2/v2.0/authorize
jwksSetUri: https://login.microsoftonline.com/<tenant-id>/discovery/v2.0/keys
tokenUri: https://login.microsoftonline.com/<tenant-id>/oauth2/v2.0/token
usernameAttribute: preferred_username
defaultRole: ROLE_GUEST
syncRoles: false
groupRoleAttribute: groupRoleAttribute
roleUserGroups: roleUserGroups
roleAdminGroups: roleAdminGroups
# userinfoUri: https://graph.microsoft.com/oidc/userinfo
userinfoUri:
# issuerUri: https://login.microsoftonline.com/a411f6bf-a08d-4aab-bef9-7f0991b2ec76/v2.0
issuerUri:
firstNameAttribute:
lastNameAttribute:
In the example above, set parameter values as follows:
primary:- Sets OpenID as the default user authentication method.
- Must be
openid.
enabled:- Enables OpenID as the user authentication method.
- Must be
true.
providerName:- Defines the name of the OpenID provider for sign-in screen.
- The value must be one word without spaces and special characters. For example,
azure.
clientName:- Defines the name of Allure TestOps as an OpenID client.
- Must match the value you set for Allure TestOps when configuring the application. For example,
testops.
clientId:- Defines the ID of Allure TestOps as an OpenID client.
- Must match the copied application ID.
clientSecret:- Defines the secret of Allure TestOps as an OpenID client.
- Must match the copied client secret.
redirectUri:- Defines the redirect URI attribute of OpenID.
- Must match the created redirect URI. For example,
https://testops.example.com/login/oauth2/code/azure.
scope:- Specifies the permissions and claims requested during authentication.
- Options:
openid,email, andprofile, but there must be at leastopenid.
authorizationGrantType:- Defines the type of grant used by Allure TestOps.
- Must be
authorization_code.
authorizationUri:- Defines the endpoint string used to initiate the authorization process with the OpenID provider.
- Must match the copied authorization endpoint (URI).
jwksSetUri:- Defines the endpoint string that provides the JSON Web Key Set (JWKS) for verifying the tokens issued by the OpenID provider.
- Must match the copied JWKS endpoint (URI).
tokenUri:- Defines the endpoint string used to obtain an access token after successful authorization.
- Must match the copied token endpoint (URI).
usernameAttribute:- Specifies the claim that Allure TestOps will use to create the username for the authenticated user.
- Options:
preferred_username,email, etc.
defaultRole:- Defines the global role of a new user who has successfully authenticated via OpenID.
- Options:
ROLE_ADMIN,ROLE_USER, orROLE_GUEST(preferred option for better control over license consumption).
syncRoles:- Determines whether global roles for the user should be assigned based on the end user’s membership in a specific group on the OpenID provider’s side.
- Options:
falseortrue.
groupRoleAttribute:Defines the name of the claim to look for the group names.
roleUserGroupscontains a list of groups whose membership grants theROLE_USERglobal role.roleAdminGroupscontains a list of groups whose membership grants theROLE_ADMINglobal role.
userinfoUri— this parameter is generally not used by Allure TestOps.issuerUri— this parameter is generally not used by Allure TestOps.firstNameAttribute:- Defines the key (name) of the claim that contains the first name of the authenticated user.
- Can be left blank to use the standard OpenID claim name for the first name.
lastNameAttribute:- Defines the key (name) of the claim that contains the last name (surname) of the authenticated user.
- Can be left blank to use the standard OpenID claim name for the surname.
This section is WIP.
Сonfigure the integration with Azure AD in the .env file. Changes in the docker-compose.yml file are not required.
# This is an example that will not work if applied without any changes.
TESTOPS_OPENID_CLIENTNAME=testops
TESTOPS_OPENID_CLIENTID=<your_client_ID_here>
TESTOPS_OPENID_CLIENTSECRET=<your_client_secret_here>
TESTOPS_OPENID_REDIRECTURI=https://<your-testops-domain>/login/oauth2/code/openid
TESTOPS_OPENID_SCOPE=openid,email,profile
TESTOPS_OPENID_USERNAMEATTRIBUTE=preferred_username
TESTOPS_OPENID_AUTHORIZATIONGRANTTYPE=authorization_code
TESTOPS_OPENID_AUTHORIZATIONURI=https://<open_id_provider_url>/somepath/openid-connect/auth
TESTOPS_OPENID_JWKSETURI=https://<open_id_provider_url>/somepath/keys
TESTOPS_OPENID_TOKENURI=https://<open_id_provider_url>/somepath/token
# next two are commented in the docker-compose.yml as these aren't used
# uncomment these in docker-compose.yml if you know what you are doing and really need using these for the integration with IdP
# TESTOPS_OPENID_ISSUERURI=https://<open_id_provider_url>/realms/<you_realm>
# TESTOPS_OPENID_USERINFOURI=https://<open_id_provider_url>/realms/<you_realm>/protocol/openid-connect/userinfo
TESTOPS_OPENID_FIRSTNAMEATTRIBUTE: first_name
TESTOPS_OPENID_LASTAMEATTRIBUTE: last_name
TESTOPS_OPENID_DEFAULTROLE=ROLE_GUEST
TESTOPS_OPENID_SYNCROLES=false
# lnked parameters for next 3 need to be commented in docker-compose.yml if TESTOPS_OPENID_SYNCROLES=false
TESTOPS_OPENID_GROUPROLEATTRIBUTE=group
TESTOPS_OPENID_GROUPAUTHORITIES_ROLEUSERGROUPS=roleUserGroups
TESTOPS_OPENID_GROUPAUTHORITIES_ROLEADMINGROUPS=roleAdminGroups
Сonfigure the integration with Azure AD in the testops.conf file at /opt/testops/conf/testops.conf.
# This is an example that will not work if applied without any changes.
ALLURE_LOGIN_PRIMARY=openid
ALLURE_LOGIN_OPENID_DEFAULTROLE=ROLE_GUEST
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_CLIENTNAME=openid
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_CLIENTID=<your_client_ID_here>
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_CLIENTSECRET=<your_client_secret_here>
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_REDIRECTURI=https://testops.example.com/login/oauth2/code/openid
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_SCOPE=openid,email,profile
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_AUTHORIZATIONGRANTTYPE=authorization_code
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_AUTHORIZATIONURI=https://login.microsoftonline.com/<tenant-id>/oauth2/v2.0/authorize
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_USERNAMEATTRIBUTE=preferred_username
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_JWKSETURI=https://login.microsoftonline.com/<tenant-id>/discovery/v2.0/keys
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_TOKENURI=https://login.microsoftonline.com/<tenant-id>/oauth2/v2.0/token
In the example above, set parameter values as follows:
ALLURE_LOGIN_PRIMARY:- Sets OpenID as the default user authentication method.
- Must be
openid.
ALLURE_LOGIN_OPENID_DEFAULTROLE:- Defines the global role of a new user who has successfully authenticated via OpenID.
- Options:
ROLE_ADMIN,ROLE_USER, orROLE_GUEST(preferred option for better control over license consumption).
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_CLIENTNAME:- Defines the name of Allure TestOps as an OpenID client.
- Must be
openid.
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_CLIENTID:- Defines the ID of Allure TestOps as an OpenID client.
- Must match the copied application ID.
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_CLIENTSECRET:- Defines the secret of Allure TestOps as an OpenID client.
- Must match the copied client secret.
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_REDIRECTURI:- Defines the redirect URI attribute of OpenID.
- Must match the created redirect URI. For example,
https://testops.example.com/login/oauth2/code/openid.
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_SCOPE:- Specifies the permissions and claims requested during authentication.
- Options:
openid,email, andprofile, but there must be at leastopenid.
SPRING_SECURITY_OAUTH2_CLIENT_REGISTRATION_OPENID_AUTHORIZATIONGRANTTYPE:- Defines the type of grant used by Allure TestOps.
- Must be
authorization_code.
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_AUTHORIZATIONURI:- Defines the endpoint string used to initiate the authorization process with the OpenID provider.
- Must match the copied authorization endpoint (URI).
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_USERNAMEATTRIBUTE:- Specifies the claim that Allure TestOps will use to create the username for the authenticated user.
- Options:
preferred_username,email, etc.
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_JWKSETURI:- Defines the endpoint string that provides the JSON Web Key Set (JWKS) for verifying the tokens issued by the OpenID provider.
- Must match the copied JWKS endpoint (URI).
SPRING_SECURITY_OAUTH2_CLIENT_PROVIDER_OPENID_TOKENURI:- Defines the endpoint string used to obtain an access token after successful authorization.
- Must match the copied token endpoint (URI).
Sign in as system account
When the default authentication method is set to OpenID, you might need to sign in to Allure TestOps as a local (system) account. To do this, use an alternative path for signing in in your browser address bar by entering the following URL: https://testops.example.com/login/system.