Users authentication with SAML and Crowd as IAM
If you are going to implement this type of authentication this action implies you clearly understand what you are doing.
Prerequisites
- You need to have administrative access to Crowd or an admin of your Crowd near you.
- You need the access to Allure Testops configuration files.
- You need to be able to apply the changes in the configuration, which could require some downtime.
- Allure Testops needs work behind HTTPS, i.e. there must be something like reverse proxy between Allure Testops and Crowd servers. Please consult your network administrator or DevOps to ensure proper configuration on the network side.
Integration of Allure Testops and Crowd as an external IAM
Given
- Allure Testops is deployed and accessible on
http://<testops>your URLs will be different. - Atlassian Crowd is available somewhere, say
https://<crowd>.
Creating new application in Crowd
In Crowd
- Jump to Applications and create something like
crowd-openid-server
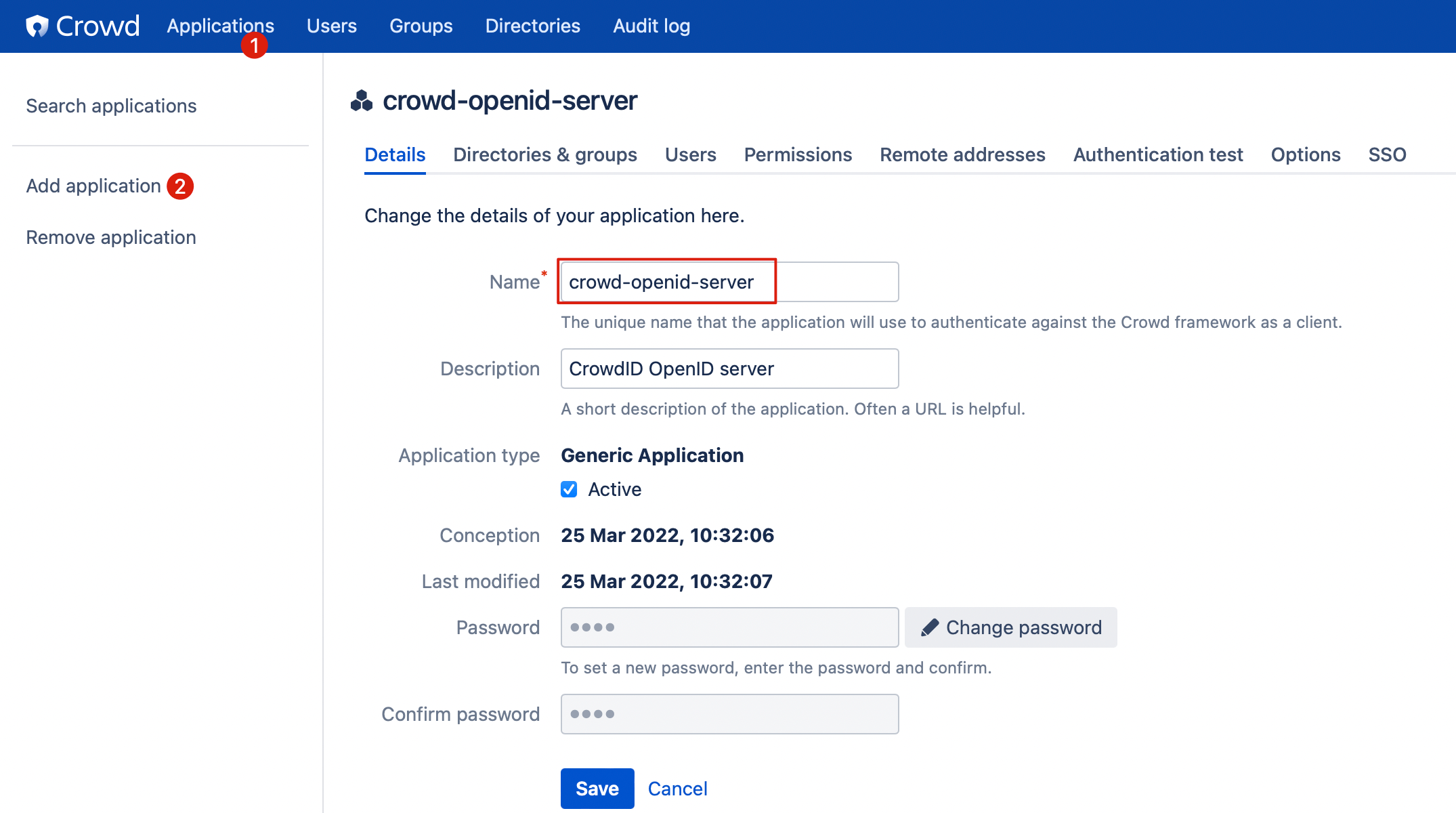
- Go to SSO tab
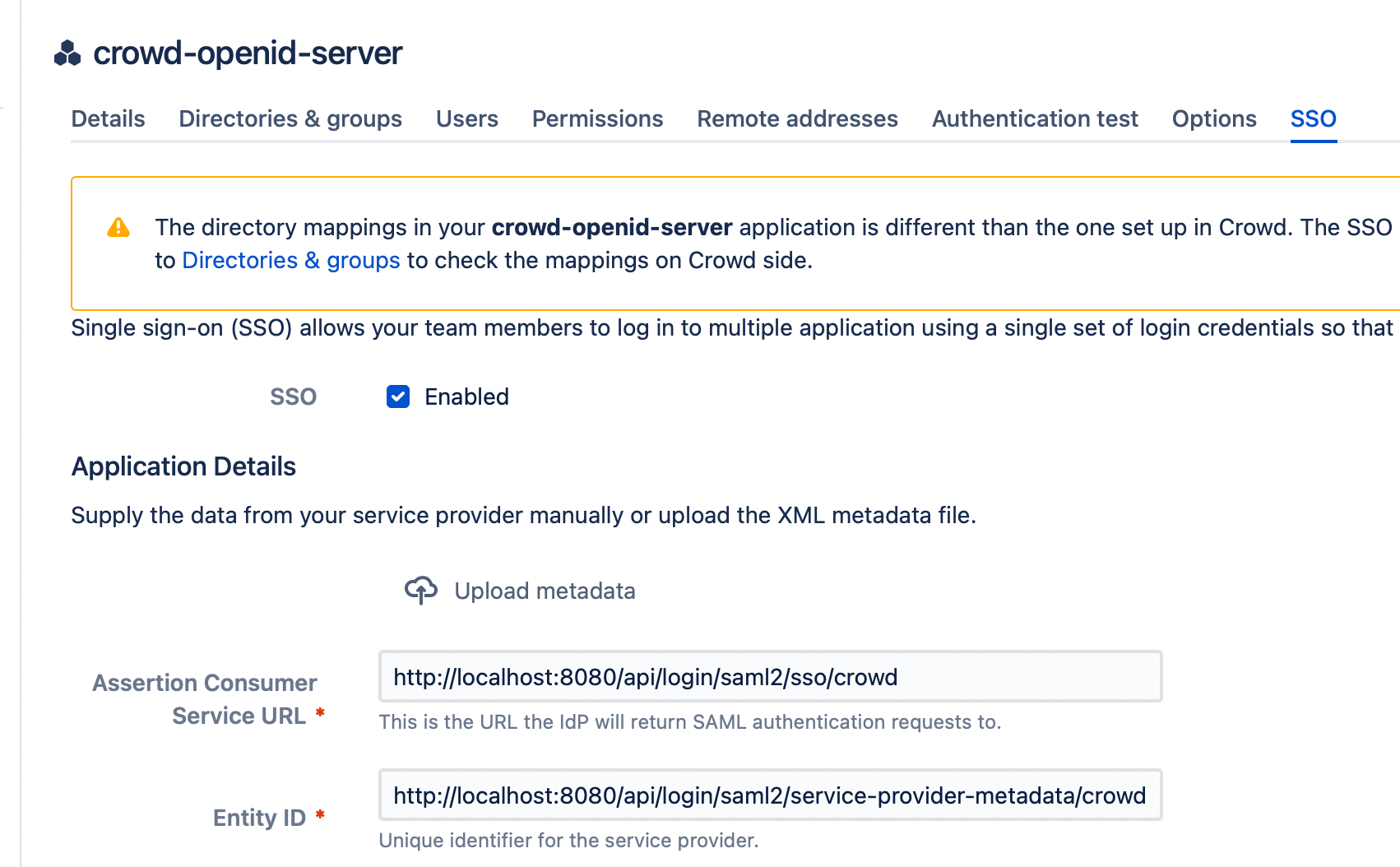
- On the SSO tab locate Download metadata button and click it.
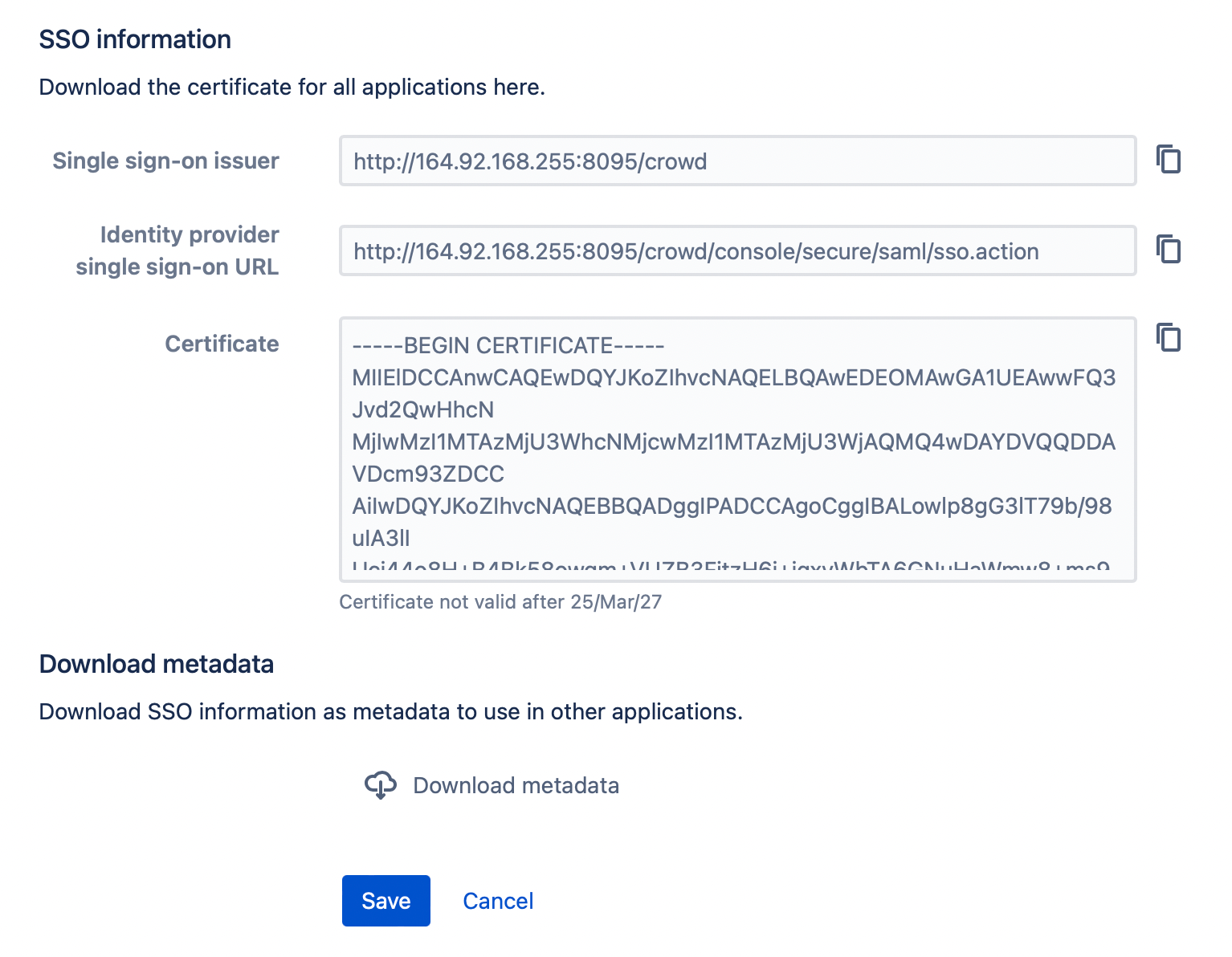
Save metadata as
metadata.xmlfor example.Next step is to update some items in the form you see.
- Say, Allure Testops lives here:
http://<testops>, so the parameters you need to update:- Assertion Consumer Service URL:
http://<testops>/api/login/saml2/sso/crowd - Entity ID:
http://<testops>/api/login/saml2/service-provider-metadata/crowd
- Assertion Consumer Service URL:
- Say, Allure Testops lives here:
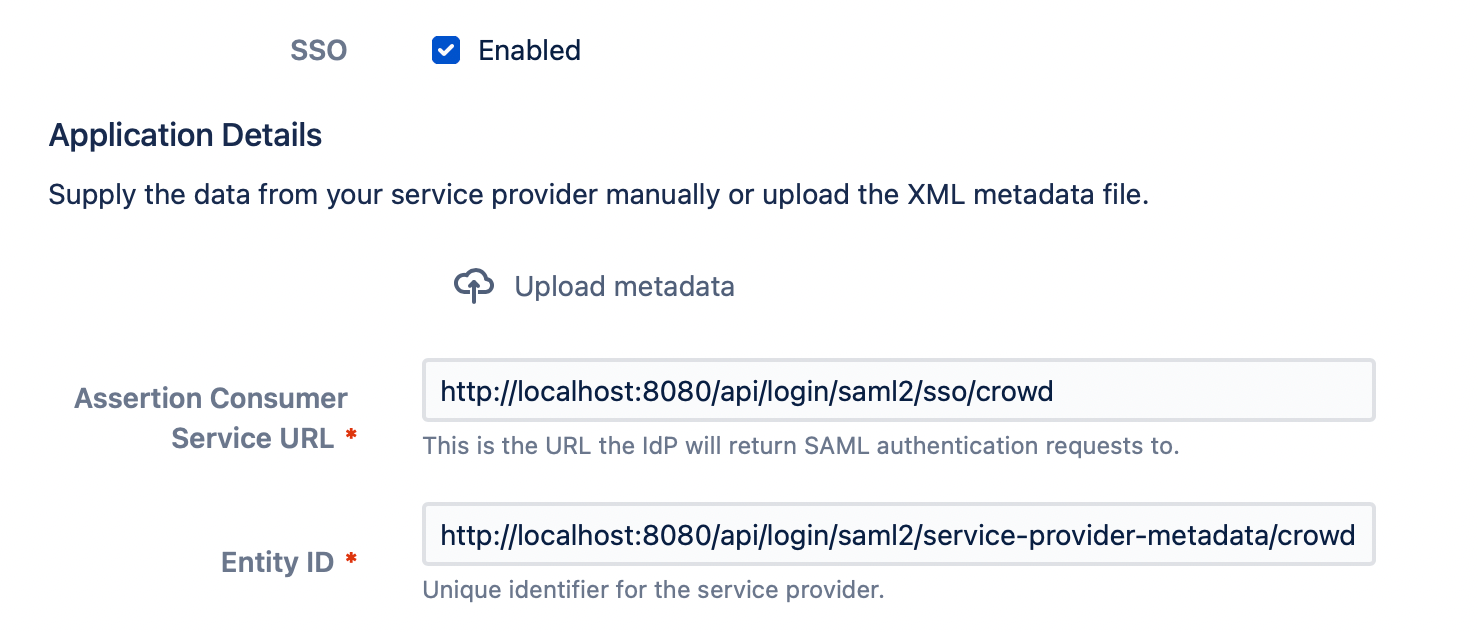
- Then press Continue
- Then press Finish
Updating Allure Testops for work with Crowd's SAML
Making a use of the metadata file
In the previous section we downloaded metadata.xml. We need mo make a use of it.
We need to make this file available for Allure Testops gateway service. This will be required for all the deployment options.
A few options here:
- File can be added to gateway's volume and it will be added to gateway parameters like file
file:///path/to/metadata.xml - File can be provided via some URL, and it will be added to gateway parameters like URL
https://some.url/metadata.xml.
Choice is yours.
Deployment in Kubernetes
For k8s deployment you need to add the parameters to open environment of gateway service of values.yaml file used to pass user's configuration to Helm.
<snip>
gateway:
env:
secret:
# security
SPRING_SECURITY_SAML2_RELYINGPARTY_REGISTRATION_CROWD_ACS_LOCATION: https://<testops>/api/login/saml2/sso/crowd
SPRING_SECURITY_SAML2_RELYINGPARTY_REGISTRATION_CROWD_ENTITYID: https://<testops>/api/login/saml2/service-provider-metadata/crowd
SPRING_SECURITY_SAML2_RELYINGPARTY_REGISTRATION_CROWD_IDENTITYPROVIDER_METADATAURI: https:///path/to/metadata.xml
<snip>
Now, to use Crowd as Identity provider, you need to update your Allure Testops configuration as usual for Kubernetes installation using Helm's commands.
After application deployment has been completed, you need to check if the authentication is working:
- Proceed to the following URL:
https://<allure>/login/saml2. - Check if the authentication is working for you.
Setting Crowd authentication as default way
This should be done only in the case, if previous check has been completed successfully.
Update uaa service settings as follows:
- add
ALLURE_LOGIN_PRIMARY: saml2
services:
<snip>
uaa:
<snip>
environment:
ALLURE_LOGIN_PRIMARY: saml2
<snip>
After this action will be completed, to log-in as a local Allure Testops user (e.g. admin), you need to access the following URL: https://<allure>/login/system.
Deployment via docker-compose
For the deployment done via docker-compose you need to update docker-compose.yml configuration file by adding the parameters to gateway service.
Updating of the configuration requires downtime to properly stop and run the application.
services:
...
gateway:
...
environment:
SPRING_SECURITY_SAML2_RELYINGPARTY_REGISTRATION_CROWD_ACS_LOCATION: https://<testops>/api/login/saml2/sso/crowd
SPRING_SECURITY_SAML2_RELYINGPARTY_REGISTRATION_CROWD_ENTITYID: https://<testops>/api/login/saml2/service-provider-metadata/crowd
SPRING_SECURITY_SAML2_RELYINGPARTY_REGISTRATION_CROWD_IDENTITYPROVIDER_METADATAURI: https:///path/to/metadata.xml
<snip>
To update Allure Testops for the usage Crowd as identity provider you need to perform the same actions you do for updating Allure Testops using docker-compose commands., i.e. 1) down, 2) then start the application using up -d
After application deployment has been completed, you need to check if the authentication is working:
- Proceed to the following URL:
https://<allure>/login/saml2. - Check if the authentication is working for you.
Setting Crowd authentication as default way
This should be done only in the case, if previous check has been completed successfully.
Update uaa service settings as follows:
- add
ALLURE_LOGIN_PRIMARY: saml2
services:
<snip>
uaa:
<snip>
environment:
ALLURE_LOGIN_PRIMARY: saml2
<snip>
After this action will be completed, to log-in as a local Allure Testops user (e.g. admin), you need to access the following URL: https://<allure>/login/system.
Deployment via packages
Update properties file /opt/allure-ee/gateway/conf/allure-gateway.properties with the following string:
spring.security.saml2.relyingparty.registration.crowd.acs.location=https://<testops>/api/login/saml2/sso/crowd
spring.security.saml2.relyingparty.registration.crowd.entityId=https://<testops>/api/login/saml2/service-provider-metadata/crowd
spring.security.saml2.relyingparty.registration.crowd.identityprovider=https:///path/to/metadata.xml
Next, you need to restart all serviced related to Allure Testops.
After applications' restart has been completed, you need to check if the authentication is working:
- Proceed to the following URL:
https://<allure>/login/saml2. - Check if the authentication is working for you.
Setting Crowd authentication as the default way
This should be done only in the case, if previous check has been completed successfully.
Update uaa service settings as follows:
- add
ALLURE_LOGIN_PRIMARY: saml2
services:
<snip>
uaa:
<snip>
environment:
ALLURE_LOGIN_PRIMARY: saml2
<snip>
After this action will be completed, to log-in as a local Allure Testops user (e.g. admin), you need to access the following URL: https://<allure>/login/system.
Setting Crowd authentication as the default way
Update properties file /opt/allure-ee/uaa/conf/allure-uaa.properties with the following string:
allure.login.primary=saml2
Setting the default role for new user registering via SAML/Crowd
Why
If no additional setting made all new users will have ROLE_USER by default and will consume 1 license.
What
To prevent new users consuming the licenses you need to define the default role for them as ROLE_GUEST, when they register in the system using SAML/Crowd. This will ensure they will have read only access by default and won't consume any licenses in the system.
How
The following parameter should be set for UAA service:
For docker-compose and Kubernetes deployment
ALLURE_LOGIN_SAML2_DEFAULTROLE: ROLE_GUEST
For the deployment using packages
allure.login.saml2.defaultRole: ROLE_GUEST